TECHNOLOGY
Unveiling the Truth: Everything You Need to Know About the Malu Trevejo Leaked Content
In malu trevejo leaked, where privacy seems like a distant memory and scandals can go viral in an instant, it’s no surprise that even celebrities fall victim to leaked content. One such celebrity who recently found herself thrust into the spotlight is none other than Malu Trevejo. Known for her youthful charm and rising music career, this young sensation has been making headlines for all the wrong reasons. In this blog post, we delve deep into the infamous Malu Trevejo leaked content scandal, uncovering how it happened, its legal implications, and its impact on her career.
Who is Malu Trevejo?
Malu Trevejo, born on October 15, 2002, is a Cuban-American singer and social media influencer. Hailing from Havana, Cuba, she gained fame through her viral videos on the popular platform Musical.ly (now known as TikTok). With her captivating dance moves and lively personality, Malu quickly amassed millions of followers.
Her rise to stardom was not limited to social media alone. Malu ventured into music and released several singles that garnered attention worldwide. Songs like “Luna Llena” and “En Mi Mente” showcased her talent as a young artist with an undeniable flair for catchy tunes.
However, it wasn’t just her musical abilities that captured people’s interest; it was also her unique style and fashion sense. Known for sporting bold hair colors and trendy outfits, Malu became a fashion icon among teenagers.
Despite being in the public eye from such a young age, Malu has faced both praise and criticism throughout her career. Some admire her confidence and talent while others question some of her controversial actions or statements.
The Leaked Content Scandal
The Leaked Content Scandal surrounding Malu Trevejo sent shockwaves through the internet and left many wondering how such private material could be exposed to the public. It was a troubling incident that raised serious concerns about online privacy and security.
Malu Trevejo, a popular social media influencer known for her music career and vibrant personality, found herself at the center of controversy when explicit content allegedly featuring her was leaked online. The leaked material quickly spread across various platforms, causing an uproar among fans and critics alike.
The exact details of how the content got leaked remain unclear. Speculation suggests that it may have been due to hacking or someone with malicious intentions gaining unauthorized access to Malu’s personal accounts or devices. Whatever the case, it highlights the importance of being vigilant about cybersecurity measures and taking steps to protect our digital presence.
In response to this shocking breach of privacy, Malu Trevejo took control of the narrative by addressing her followers directly on social media platforms. She acknowledged the situation while expressing her disappointment, frustration, and determination not to let this define her career moving forward.
Leaking personal content without consent is not only morally wrong but also illegal in many jurisdictions. Depending on local laws regarding privacy rights and revenge porn, those responsible for leaking such material could face severe legal consequences if identified.
This scandal undoubtedly had an impact on Malu Trevejo’s career. While some fans stood by her side offering support during this challenging time, others criticized or distanced themselves from her due to their own judgments about personal choices she may have made privately.
The entire incident serves as a reminder that we should all be mindful of our digital footprint and take precautions against cyber threats. Protecting sensitive information requires strong passwords, secure networks, regular software updates, cautious sharing habits online – especially with intimate photos or videos – as well as understanding platform privacy settings.
How Did the Content Get Leaked?
The leaking of personal content is a serious breach of privacy, and Malu Trevejo found herself at the center of such a scandal. But how did her private photos and videos end up in the public domain? The answer lies in the ever-present dangers of online security.
One possible explanation is that Malu’s accounts were hacked. Cybercriminals are constantly finding new ways to infiltrate people’s digital lives, especially those who have a large following like Malu Trevejo. They may have used sophisticated techniques to gain unauthorized access to her devices or social media accounts.
Another possibility is that someone close to Malu leaked the content intentionally. Unfortunately, celebrities often fall victim to betrayal from those they trust most. It only takes one person with ill intentions and access to sensitive material for it to be shared without consent.
There’s also the chance that Malu unintentionally shared these private moments with someone she thought she could trust, only for them to betray her by leaking them online. This serves as a stark reminder that we must always exercise caution when sharing intimate content with anyone, even if we believe they will keep it confidential.
Additionally, there are instances where hackers exploit vulnerabilities in platforms themselves, allowing them unauthorized access not just to individual accounts but potentially multiple users’ private information simultaneously.
The Aftermath and Response from Malu Trevejo
The aftermath of the leaked content scandal involving Malu Trevejo was nothing short of chaotic. As soon as the private photos and videos were made public, they spread like wildfire across social media platforms and gossip websites. The invasion of her privacy left Trevejo shocked, hurt, and deeply violated.
In response to the leak, Malu Trevejo took to social media to address the situation head-on. She expressed her anger and frustration at those responsible for sharing her intimate moments without consent.
Trevejo’s response gained support from fans who rallied around her in solidarity against online harassment and violation of privacy. Many praised her bravery for speaking out about such a personal ordeal in a public forum.
Despite facing immense backlash from some quarters, others stood by Malu Trevejo during this difficult time. They applauded her courage in confronting adversity head-on instead of hiding away or succumbing to shame.
As we can see from this situation, leaked content can have significant emotional consequences on its victims’ lives.
Legal Implications of Leaked Content
The leaking of personal content without consent can have serious legal consequences. In the case of Malu Trevejo, the unauthorized release of her private photos and videos raises important legal questions.
One key aspect is privacy law. Individuals have a right to control their own personal information, including intimate images and videos. When such content is leaked without permission, it constitutes a violation of privacy rights.
The unauthorized distribution and reproduction of copyrighted material can lead to legal action against those responsible for the leak.
Furthermore, there may be potential criminal charges involved in cases like this.
It’s worth noting that each jurisdiction has its own specific laws regarding privacy and intellectual property rights. Therefore, the legal implications surrounding leaked content will vary depending on where it occurred.
When personal content is leaked without consent, it not only violates an individual’s privacy but also carries significant legal repercussions.
Impact on Malu Trevejo’s Career
The leaked content scandal involving Malu Trevejo has undoubtedly had a significant impact on her career. As a popular social media influencer and rising star in the music industry, this unfortunate incident has brought unwanted attention and scrutiny to her personal life.
The leaked content has tarnished Malu’s reputation. It is challenging for any public figure to recover from such an invasion of privacy.
This can lead to lost opportunities for endorsements, sponsorships, and collaborations that could have further boosted her career.
Additionally, the leak has also resulted in negative backlash from both fans and critics alike.
With time, strategic choices, and proper crisis management skills in place, there is still hope for Malu Trevejo’s career recovery.
Lessons Learned and Online Safety Tips
First and foremost, it is crucial to be mindful of what we share online. Think twice before posting personal or sensitive information that could potentially be used against you. Remember that once something is out there, it can be difficult to completely erase.
Always consider your audience when sharing content. Adjust your privacy settings accordingly and only share with trusted individuals. Be aware that even within private circles, leaks can still happen.
Furthermore, practice good password hygiene by using strong passwords for all your accounts. Avoid using easily guessable information such as birthdays or pet names. Enable two-factor authentication whenever possible for an added layer of security.
Conclusion:
As we wrap up our exploration of the Malu Trevejo leaked content scandal, it is important to reflect on the lessons learned and consider online safety tips that can help protect individuals from similar situations.
Additionally, this unfortunate situation raises awareness about the legal implications surrounding leaked content. It is vital for individuals to understand their rights and seek legal recourse when necessary. Cyber laws are constantly evolving, and staying informed about these changes can better equip us to navigate potential issues.
Furthermore, this incident has undoubtedly had a significant impact on Malu Trevejo’s career.
FAQ’s
Q: Who is Malu Trevejo?
A: Malu Trevejo is a popular social media personality, singer, and model. She gained fame through platforms like TikTok and Instagram, where she has amassed millions of followers.
Q: What is the leaked content scandal involving Malu Trevejo?
A: The leaked content scandal refers to the unauthorized release of explicit videos and photos featuring Malu Trevejo.
Q: How did the content get leaked?
A: The exact details of how the content got leaked remain unknown. However, it’s believed that someone hacked into Malu’s personal accounts or devices to obtain these private materials.
Q: What was Malu Trevejo’s response to the leaked content scandal?
A: Following the leak, Malu took to social media platforms like Twitter to address the situation directly.
Q: Are there any legal implications for leaking someone’s private content?
A: Yes, leaking someone’s private content without their consent is a violation of their privacy rights. It can lead to legal consequences for those involved in hacking or distributing such material without permission.
Q: How has this incident impacted Malu Trevejo’s career?
A: The incident has undoubtedly had a negative impact on both her personal life and professional career.
TECHNOLOGY
Unlocking the Power of Plangud: A Comprehensive Guide

Enter Plangud a revolutionary tool designed to streamline your planning and productivity like never before. Whether you’re an entrepreneur juggling multiple projects or a student managing assignments, Plangud offers a unique approach to organization that can transform how you work.
Imagine having all your tasks, deadlines, and goals in one place. Picture a system that not only helps you plan but also motivates you to achieve more each day. This is the power of Plangud. It combines simplicity with functionality, making it accessible for anyone who wants to enhance their workflow.
Curious about what makes this platform so special? Let’s dive deeper into the world of Plangud and explore how it can revolutionize your daily routine and boost your productivity!
The Benefits of Using Plangud
Plangud offers a range of benefits that can transform how you approach tasks. Its intuitive interface makes it easy for anyone to navigate and utilize effectively. This simplicity encourages more users to adopt the platform seamlessly.
One major advantage is its ability to enhance collaboration among team members. Everyone stays on the same page, reducing misunderstandings and boosting productivity. Real-time updates ensure that changes are visible instantly, fostering a sense of teamwork.
Additionally, Plangud promotes better time management through its scheduling features. Users can prioritize tasks efficiently, ensuring deadlines are met without unnecessary stress.
Moreover, the analytics tools provide valuable insights into progress and performance metrics. These data-driven reports help identify areas for improvement and streamline workflows further.
Using Plangud ultimately leads to increased efficiency in both individual and group projects. The platform’s versatility caters to diverse needs across various industries.
How to Get Started with Plangud
Getting started with Plangud is easy and straightforward. First, visit the official website to create an account. Registration typically requires just a few basic details.
Once you’re signed up, take some time to explore the platform’s features. Familiarize yourself with its user interface and tools designed for planning and organization.
Next, set your goals. Define what you want to achieve using Plangud—whether it’s managing projects or personal tasks.
Consider integrating existing data or materials into your new workspace. This can save time and help streamline your workflow from the get-go.
Don’t hesitate to check out tutorials or guides within the platform. These resources provide valuable insights that can enhance your experience right away.
Start small by creating simple plans before diving into more complex projects. Build confidence gradually while adapting Plangud to fit your unique needs.
Tips for Maximizing Productivity with Plangud
To truly harness the power of Plangud, start by setting clear and achievable goals. Break larger tasks into smaller steps to maintain focus and momentum.
Utilize the scheduling feature effectively. Block out specific times for different projects. This helps create a structured workflow that prevents distractions.
Leverage collaboration tools within Plangud. Engage with your team by sharing ideas or progress updates in real time. Communication is crucial for maintaining productivity.
Incorporate regular check-ins with yourself or your team to assess what’s working and what isn’t. Adjustments may be necessary along the way.
Familiarize yourself with keyboard shortcuts available in Plangud. They can significantly speed up navigation, allowing you more time for actual work rather than clicking around aimlessly.
Integrating Plangud into Your Daily Routine
Integrating Plangud into your daily routine can transform how you manage tasks. Start by setting aside a few minutes each morning to outline your day using the platform. This helps prioritize important activities.
Consider syncing Plangud with other tools you already use. Whether it’s email or calendar apps, integration streamlines processes and keeps everything in one place.
During work hours, take advantage of reminders for deadlines and meetings. This feature ensures that nothing slips through the cracks while keeping you focused on what matters most.
Make it a habit to review your progress at the end of each day. Reflecting on accomplishments fosters motivation and identifies areas for improvement.
Encourage colleagues or team members to adopt Plangud as well. A shared approach enhances collaboration and accountability within projects.
Case Studies: Successful Implementation of Plangud in Various Industries
Plangud has made waves across various industries by enhancing workflow and productivity. In the tech sector, a leading software company adopted Plangud to streamline project management. The result? A 30% reduction in time spent on task allocation.
In healthcare, a hospital integrated Plangud for scheduling staff shifts. This shift led to improved patient care through better resource management, allowing nurses and doctors to focus on what truly matters—patient well-being.
Retail businesses have also reaped benefits. One prominent chain utilized Plangud for inventory tracking and supply chain coordination. They experienced significant cost savings and minimized stockouts that often frustrated customers.
Even educational institutions embraced this tool. A university used Plangud to coordinate course offerings, resulting in higher student satisfaction rates due to streamlined class schedules and resources.
These examples showcase how versatile Plangud can be when tailored effectively across different fields.
Common Challenges and Solutions When Using Plangud
Using Plangud can transform productivity, but it’s not without its challenges. One common hurdle is user resistance. Many people hesitate to adopt new tools, fearing disruption in their workflow.
Training sessions and onboarding tutorials can help ease this transition. Comprehensive resources empower users to explore Plangud’s features confidently.
Another issue is integration with existing systems. Smooth functionality depends on seamless collaboration among various tools. It’s crucial to invest time in setting up integrations properly.
Technical glitches or bugs may arise during implementation as well. Regular updates from the developers often address these issues promptly, so staying informed about upgrades is essential.
Some users struggle with overwhelmed project views due to excessive task details. Customizing dashboards allows individuals to focus on what matters most while reducing visual clutter for increased clarity and efficiency.
Conclusion
Plangud has emerged as a powerful tool for individuals and businesses alike. Its versatility allows users to tailor their planning and productivity strategies effectively. By understanding how Plangud works, you open the door to numerous benefits that can transform your daily operations.
Getting started is straightforward, making it accessible even for those who may not consider themselves tech-savvy. With some initial setup and exploration of its features, users can begin reaping the rewards of enhanced organization and efficiency.
Maximizing productivity with Plangud involves integrating its various functionalities into your workflow seamlessly. Utilizing tips like setting specific goals or utilizing reminders can elevate your experience further. As you incorporate Plangud into your daily routine, you’ll find new ways to stay on track while minimizing stress.
TECHNOLOGY
Infector virus: How They Spread and Impact Our Lives
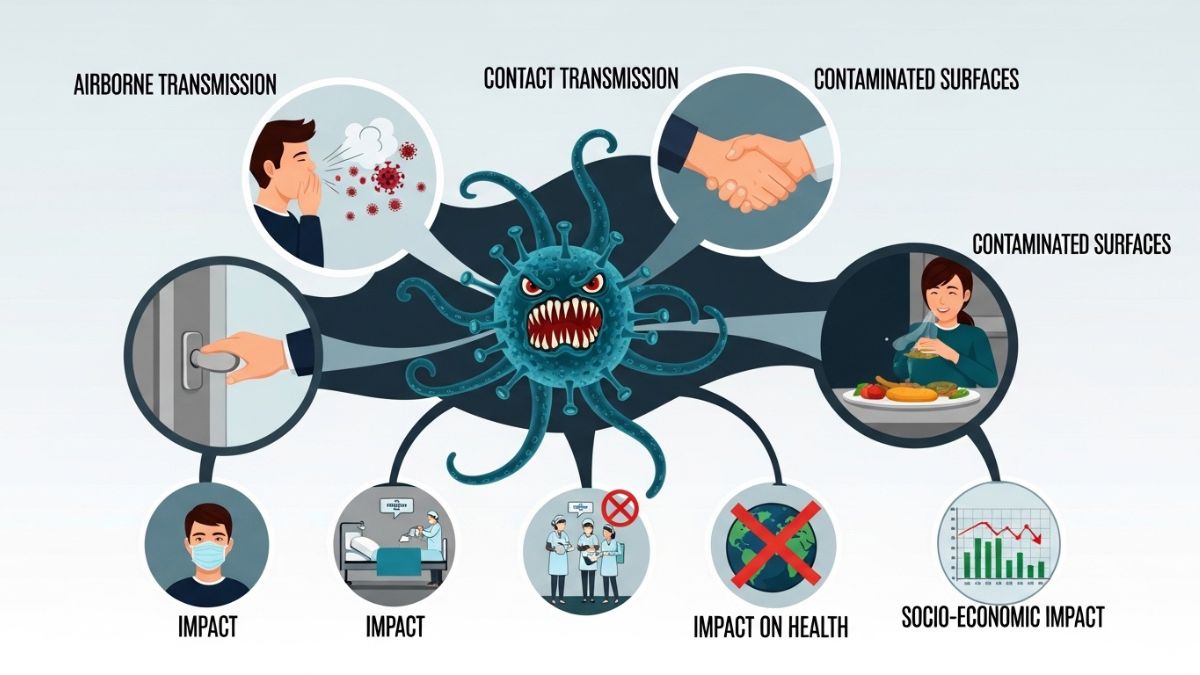
Viruses are tiny entities that can have a massive impact on our lives. From the common cold to more severe illnesses, these microorganisms are everywhere. They can spread quickly and affect millions of people in a matter of days. Among them, infector viruses stand out due to their ability to invade host cells and replicate efficiently.
Understanding how these viruses operate is crucial in today’s world, where global travel and interconnectedness make outbreaks more likely than ever. As we dive into the specifics of infector viruses, we’ll uncover how they spread and why it matters for our health and safety. Join us as we explore this fascinating yet concerning aspect of microbiology that affects us all.
What is an infector virus?
An infector virus is a type of microorganism that can invade living cells. Once inside, it hijacks the cell’s machinery to replicate itself. This process often leads to cell damage or death.
These viruses come in various shapes and sizes. Some are simple, while others have complex structures with protective coatings. Their ability to adapt makes them particularly challenging for our immune systems.
Infector viruses can affect a wide range of organisms, from humans and animals to plants and bacteria. They play significant roles in ecosystems but can also cause serious health issues.
Understanding how these viruses operate helps researchers develop vaccines and treatments. The study of infector viruses is crucial for public health as we navigate emerging threats around the globe.
How do infector viruses spread?
Infector viruses can spread through various means, making them particularly challenging to control. One primary mode of transmission is direct contact. When an infected person touches another individual or a surface, the virus can transfer easily.
Airborne particles also play a significant role in spreading these viruses. As we breathe, talk, or cough, tiny droplets containing the virus become suspended in the air. Others may inhale these droplets without even realizing it.
Another common way infector viruses propagate is via contaminated surfaces and objects. Viruses can survive on doorknobs, phones, and utensils for hours or even days. Touching these surfaces and then touching your face increases the risk of infection dramatically.
Some infector viruses require vectors like insects to transmit between hosts. Mosquitoes are well-known carriers that facilitate this type of spread by biting an infected host and then transferring the virus to others they bite thereafter.
The effects of infector viruses on our health
Infector viruses can have profound effects on human health. They enter the body and exploit our cells for reproduction, often leading to illness. Symptoms may range from mild discomfort to severe conditions that require hospitalization.
Influenza is a prime example of an infector virus that causes seasonal outbreaks. It can lead to respiratory problems, fever, and fatigue. For vulnerable populations like the elderly or those with underlying health issues, these viruses pose even greater risks.
Moreover, some infector viruses can result in long-term health consequences. Conditions such as chronic fatigue syndrome or post-viral syndromes can linger well after initial infection has subsided.
The psychological impact shouldn’t be overlooked either; fear of viral outbreaks can contribute to anxiety and stress among communities. Awareness and understanding are crucial in navigating these challenges effectively.
Recent outbreaks of infector viruses
Recent outbreaks of infector viruses have captured global attention and concern. The rise in new strains has highlighted our vulnerability to these microscopic foes.
For instance, the emergence of novel coronaviruses has led to significant disruptions worldwide. Each outbreak brings about unique challenges in containment and response efforts.
Influenza variants also continue to circulate, reminding us that vigilance is necessary year-round. Health organizations are constantly monitoring changes in viral behavior and transmission rates.
In regions with dense populations, the spread can be rapid and devastating. Vaccination campaigns play a crucial role in mitigating risks during peak seasons.
Social distancing measures have become commonplace during such crises, but they come with economic costs as well. The interconnectedness of our world means that an outbreak anywhere can quickly turn into a global issue.
Efforts for better surveillance systems are underway to track these viruses more effectively, aiming for quicker responses when outbreaks occur.
How to protect against infector viruses
Staying vigilant is key when it comes to protecting yourself from infector viruses. Start with good hygiene practices. Frequent hand washing with soap for at least 20 seconds can significantly reduce your risk of infection.
Consider using hand sanitizer, especially in crowded places where soap and water aren’t available. Choose one that contains at least 60% alcohol for maximum effectiveness.
Vaccination plays a crucial role as well. Stay updated on recommended vaccines that protect against specific viruses prevalent in your area or traveling destination.
Avoid close contact with sick individuals whenever possible. Maintain a safe distance during outbreaks, and don’t hesitate to wear masks if advised by health authorities.
Keep informed about local health advisories and follow any guidelines provided by public health officials. Awareness helps you make better choices to stay healthy amidst potential threats from infector viruses.
Conclusion
Viruses are tiny entities that wield significant influence over our lives. Among them, infector viruses stand out due to their ability to cause illness and outbreaks. Understanding these viruses is crucial for safeguarding ourselves and our communities.
An infector virus is a type of pathogen known for its capacity to invade host cells, replicate, and spread throughout populations. They can be responsible for a broad spectrum of diseases, from mild infections like the common cold to more severe illnesses such as COVID-19 or influenza.
These viruses spread through various means—airborne transmission via respiratory droplets, direct contact with infected surfaces, or even through bodily fluids. Their adaptability allows them to find new hosts quickly and efficiently.
The impact on health can vary significantly depending on the specific virus in question. Symptoms might range from mild discomfort to severe illness requiring hospitalization. Vulnerable groups such as the elderly or those with pre-existing conditions often face heightened risks.
TECHNOLOGY
Exploring Ingebim: The Ultimate Guide to Understanding Its Impact

In a world driven by innovation, few concepts capture the imagination quite like Ingebim. This cutting-edge technology is changing how we think about data management and operational efficiency. As businesses continue to look for smarter solutions, understanding Ingebim has become essential. But what exactly is it? And how does it influence industries today?
From its humble beginnings to its current revolutionary applications, the journey of Ingebim is as fascinating as it is impactful. Whether you’re a business leader seeking competitive advantage or simply curious about technological advancements, this guide will take you through everything you need to know about Ingebim. Buckle up; we’re diving deep into the realm of possibilities!
What is Ingebim?
Ingebim is a powerful tool designed to streamline data integration and business intelligence processes. At its core, it serves as a bridge between various data sources, allowing organizations to gather insights with ease.
Think of Ingebim as the ultimate connector. It takes disparate systems and transforms them into cohesive platforms for analysis. This allows users to harness valuable information without grappling with complex coding or manual data entry.
The technology utilizes advanced algorithms and machine learning techniques that enhance decision-making efficiency. Its user-friendly interface enables even non-technical users to navigate the system effortlessly.
With Ingebim, businesses can automate tasks that once required substantial human effort. This leads not only to time savings but also improved accuracy in reporting and analytics. As more companies adopt this innovative solution, its significance continues to grow across industries worldwide.
The History and Evolution of Ingebim
Ingebim traces its roots back to the early digital landscape, where data management and analysis were burgeoning fields. Initially focused on basic databases, it evolved with technology’s rapid pace.
As businesses recognized the potential of big data, Ingebim adapted by integrating advanced algorithms and machine learning techniques. This transition marked a pivotal moment in its evolution, allowing for deeper insights and predictions based on vast datasets.
The 2010s witnessed an explosion in cloud computing. Ingebim capitalized on this shift by offering scalable solutions that catered to organizations of all sizes.
Today, it stands as a versatile tool that combines analytics with user-friendly interfaces. Its growth reflects ongoing innovations in data science and the increasing demand for intelligent decision-making tools across various industries.
How Ingebim Works
Ingebim operates through a sophisticated network of algorithms and data analysis techniques. At its core, it leverages machine learning to interpret vast amounts of information.
The system begins by collecting diverse data sets from various sources. This can include user behavior, environmental factors, or industry trends. Once gathered, the data undergoes rigorous processing and cleansing to ensure accuracy.
Next comes the analysis phase. Here, Ingebim uses predictive modeling to uncover patterns that might not be immediately obvious. It identifies correlations that can inform decision-making processes across different sectors.
Moreover, Ingebim’s adaptability allows it to adjust as new information becomes available. This continuous learning helps refine outcomes over time. Users benefit from real-time insights that drive strategic initiatives forward without delay.
Real-life Examples of Successful Ingebim Implementation
Companies across various industries have begun to harness the power of Ingebim, achieving remarkable results. One notable example is a retail giant that integrated Ingebim into its supply chain management. The technology streamlined operations, reducing delivery times and increasing customer satisfaction.
In the healthcare sector, a hospital network used Ingebim to enhance patient data management. This implementation improved communication among staff and led to faster diagnosis and treatment options for patients.
Another interesting case comes from finance. A fintech startup utilized Ingebim for fraud detection in real-time transactions. By analyzing patterns swiftly, the company minimized losses significantly while gaining consumer trust.
These examples illustrate how diverse sectors can leverage Ingebim’s capabilities, transforming challenges into opportunities for growth and innovation. Each success story adds to the growing narrative of what this technology can accomplish when applied thoughtfully.
The Benefits and Drawbacks of Using Ingebim
Ingebim offers numerous advantages that can significantly enhance operational efficiency. By streamlining processes, it helps organizations save time and reduce costs. Many users report improved data accuracy as well.
However, there are challenges to consider. Implementation can be complex, often requiring extensive training for staff. This learning curve may temporarily disrupt productivity.
Security is another concern. Storing sensitive information within Ingebim systems raises risks related to data breaches. Organizations must invest in robust cybersecurity measures to mitigate these threats.
Moreover, reliance on technology can lead to vulnerabilities if the system experiences downtime or fails unexpectedly. Balancing automation with human oversight becomes crucial in such scenarios.
Weighing these benefits against drawbacks is essential for companies considering Ingebim adoption. Understanding both sides will aid informed decision-making and strategic planning.
Ethical Concerns Surrounding Ingebim
The rise of Ingebim brings with it a host of ethical concerns. Privacy is at the forefront. As data collection becomes more sophisticated, individuals may unknowingly surrender their personal information.
There’s also the risk of bias in decision-making processes powered by Ingebim systems. If the underlying algorithms are flawed or trained on skewed data, outcomes could disproportionately affect certain groups.
Transparency is another significant issue. Many users lack a clear understanding of how Ingebim functions and how decisions are made based upon its analyses.
Moreover, accountability becomes murky when automated systems operate independently. Who takes responsibility for mistakes? The developers? The users?
As organizations increasingly adopt Ingebim technology, there looms an ethical dilemma around dependency on machines versus human judgment. Striking a balance between efficiency and moral considerations remains crucial as we navigate this evolving landscape.
Future Predictions for the Growth of Ingebim
As technology continues to advance, the growth of Ingebim appears promising. Experts forecast an increased adoption across various sectors, particularly in healthcare and finance. This trend is driven by a rising demand for efficient data management and analysis.
Furthermore, advancements in artificial intelligence could enhance Ingebim’s capabilities significantly. With machine learning integration, organizations may leverage real-time insights more effectively than ever before.
The global push for digital transformation also plays a crucial role. Companies are recognizing the need to streamline operations through innovative solutions like Ingebim.
Additionally, regulatory frameworks are likely to evolve alongside technological progress. This will create both challenges and opportunities as industries adapt to new standards surrounding data usage.
Emerging markets might lead this charge too. As they invest in infrastructure, Ingebim’s reach can expand further into previously untapped regions.
Conclusion
As we delve into the complexities of Ingebim, it becomes clear that this innovative tool is reshaping industries across the board. Its unique functionalities offer organizations the chance to streamline processes and enhance efficiency. Understanding its history allows us to appreciate how far technology has come, paving the way for future advancements.
The real-life examples highlight just how transformative Ingebim can be when implemented successfully. However, it’s crucial to weigh both benefits and drawbacks carefully. The ethical concerns surrounding data privacy and security remind us of our responsibilities as users.
Looking ahead, predictions about Ingebim’s growth suggest an exciting trajectory filled with potential innovations. As businesses continue to adapt and integrate new technologies like Ingebim into their operations, staying informed will be essential for maximizing its advantages while navigating any associated challenges.
-

 HEALTH2 years ago
HEALTH2 years agoTransformative Health Solutions: Unveiling the Breakthroughs of 10x Health
-

 GENERAL2 years ago
GENERAL2 years agoDiscovering the Artistic Brilliance of Derpixon: A Deep Dive into their Animation and Illustration
-

 Posts2 years ago
Posts2 years agoSiegel, Cooper & Co.
-

 Lifestyle2 years ago
Lifestyle2 years agoPurenudism.com: Unveiling the Beauty of Naturist Lifestyle
-

 FASHION2 years ago
FASHION2 years agoThe Many Faces of “λιβαισ”: A Comprehensive Guide to its Symbolism in Different Cultures
-

 Lifestyle2 years ago
Lifestyle2 years agoBaddieHub: Unleashing Confidence and Style in the Ultimate Gathering Spot for the Baddie Lifestyle
-

 Entertainment2 years ago
Entertainment2 years agoGeekzilla Podcast: Navigating the World of Pop Culture, Gaming, and Tech
-

 Lifestyle2 years ago
Lifestyle2 years agoSandra orlow: Unraveling the Story of an Iconic Figure
