TECHNOLOGY
What Are The Different Layers Of Network Security?

In today’s interconnected digital landscape, where data flows freely across networks, the need for robust network security measures has become paramount. As businesses, governments, and individuals rely more heavily on digital infrastructure, the risk of unauthorized access, data breaches, and cyber-attacks looms ever larger. To safeguard against these threats, a multi-layered approach to network security is essential.
Network security encompasses a comprehensive set of technologies, processes, and practices designed to protect data and resources’ integrity, confidentiality, and availability within a network. These protective measures operate across different layers, each addressing specific vulnerabilities and threats, creating a defense-in-depth strategy that enhances overall security posture. Consult with IT Consulting Denver experts to create an effective network security strategy for your business.
In this article, we will explore why network layer security is important and different network security layers.
Why are Network Layers Important?
Network layers are essential components in the design and function of computer networks. They provide a structured way to organize and manage the different functions that are required for communication between devices. Each layer serves a specific purpose: data encapsulation, error detection, or routing. Dividing network functionality into layers makes it easier to understand and troubleshoot network issues.
Additionally, network layers facilitate interoperability between different systems and devices by providing a common framework for communication. This standardized approach helps networks scale effectively and support various applications and services. In essence, network layers play a crucial role in ensuring modern computer networks’ efficiency, reliability, and security.
8 Different Layers Of Network Security
-
Physical Security
Physical security is a fundamental layer of network security that focuses on protecting the physical assets and infrastructure of an organization. This includes securing the premises where network equipment is housed, such as data centers, server rooms, and wiring closets.
Physical security measures may include access control systems, surveillance cameras, biometric scanners, locks, and alarms to prevent unauthorized access or tampering with critical network components. By safeguarding the physical environment in which network resources are located, organizations can mitigate the risk of theft, vandalism, or other physical threats that could compromise the integrity and availability of their networks.
-
Perimeter Security
Perimeter security is a fundamental network security layer that serves as the first line of defense against external threats. It encompasses firewalls, intrusion detection systems, and virtual private networks to safeguard the network from unauthorized access and malicious activities.
By establishing strong perimeter security measures, organizations can monitor and control traffic entering and leaving their networks, reducing the risk of potential cyberattacks and data breaches. Implementing robust perimeter security protocols is essential in maintaining the integrity and confidentiality of sensitive information within an organization’s network infrastructure.
-
Network Access Control (NAC)
Network Access Control (NAC) is a critical component of network security that helps organizations regulate and secure access to their networks. By implementing NAC, businesses can enforce policies that determine which devices are allowed to connect to the network and what level of access each device is granted. This proactive approach to network security ensures that only authorized users and devices can access sensitive information, reducing the risk of data breaches and unauthorized access.
NAC solutions typically involve authentication mechanisms, endpoint security checks, and monitoring capabilities to assess and manage network access continuously. Proper implementation of NAC can significantly enhance an organization’s overall cybersecurity posture by adding a layer of defense against potential threats.
-
Network Segmentation
Network segmentation is crucial to ensuring robust network security. By dividing a network into smaller segments, organizations can enhance control over their data and resources, limiting unauthorized access to sensitive information. This practice also helps contain potential security breaches by isolating compromised segments from the rest of the network.
Implementing network segmentation requires careful planning and configuration to establish secure zones within the network architecture. Organizations can strengthen their overall cybersecurity posture and mitigate the risk of widespread data breaches by segmenting networks based on criteria such as user roles, departments, or applications.
-
Secure Communication Protocols
Secure communication protocols are critical to network security, ensuring that data transmitted between devices remains confidential and integral. Implementing protocols such as SSL/TLS for encrypting data in transit can help prevent unauthorized access and eavesdropping on sensitive information.
Additionally, secure email protocols like S/MIME or PGP can safeguard email communications from interception and tampering. Incorporating robust, secure communication protocols into your network infrastructure can enhance your organization’s overall security posture and protect against potential cyber threats.
-
Application Security
Application security is a crucial layer of network security that focuses on securing software applications from various threats and vulnerabilities. It involves implementing measures to protect applications throughout their lifecycle, from the design and development stages to deployment and maintenance.
Application security aims to prevent unauthorized access, data breaches, and other cyberattacks that target vulnerabilities within the application itself. Organizations can enhance their overall network security posture by conducting regular security assessments and code reviews, implementing secure coding practices, and mitigating risks associated with potential application-related exploits.
-
Endpoint Security
Endpoint security is a critical layer of network security that protects end-user devices such as laptops, desktops, and mobile devices from cyber threats. These endpoints serve as entry points to the network and are vulnerable to various attacks, making it essential to implement robust security measures.
Endpoint security solutions typically include antivirus software, firewalls, encryption tools, and intrusion detection systems to safeguard against malware, phishing attempts, unauthorized access, and data breaches. By securing endpoints effectively, organizations can ensure the integrity and confidentiality of their networks and sensitive information.
-
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a critical levels of network security that focuses on identifying, monitoring, and protecting sensitive data from unauthorized access or exfiltration. Organizations can prevent data breaches, comply with regulatory requirements, and safeguard their intellectual property by implementing DLP solutions.
DLP technologies use a combination of content inspection, contextual analysis, and user activity monitoring to detect and prevent the unauthorized transmission of sensitive information. Through policy enforcement and encryption mechanisms, DLP helps organizations mitigate the risks associated with data loss and maintain the confidentiality and integrity of their valuable assets. If you want to secure your business data, contact the Managed IT Services Denver team.
In Conclusion
It is crucial to understand the various layers of network security in order to protect digital assets and ensure the integrity of networks in today’s interconnected world. Organizations should adopt a comprehensive approach that includes both preventive and reactive measures across all layers, from physical security to application-level protection, to effectively mitigate risks and defend against a wide range of threats. However, it is important to recognize that network security is not a one-time solution but an ongoing process that requires assessment, adaptation, and investment in advanced technologies and best practices.
TECHNOLOGY
Unpacking Banflix: What Sets It Apart in the Streaming Universe

Welcome to the world of Banflix, a new contender shaking up the streaming landscape. In an era where countless platforms vie for your attention, Banflix brings something fresh and exciting to the table. But what exactly is it? Imagine a service that not only curates content but also tailors experiences to meet diverse tastes and preferences. Whether you’re a fan of indie films, international shows, or popular blockbusters, this platform aims to cater to everyone.
As we dive deeper into what makes Banflix unique in the crowded streaming universe, prepare for insights on its content diversity, user-friendly features, and how it’s influencing industry trends. Let’s unpack the allure of Banflix together!
How Banflix differs from other streaming services
Banflix sets itself apart from traditional streaming platforms through its unique content acquisition strategy. While many services focus on original programming or licensing popular titles, Banflix emphasizes niche genres and underrepresented voices. This leads to a richer variety of shows and movies that you won’t find elsewhere.
The platform also prioritizes user engagement by allowing subscribers to create personalized playlists. Viewers can curate their own viewing experiences, making it more interactive than just passive watching.
Another distinguishing feature is the flexible subscription model. Unlike competitors locked into annual commitments, Banflix offers monthly plans with no hidden fees or long-term contracts, appealing to budget-conscious consumers.
Moreover, Banflix’s algorithm promotes discovery over trending content. It suggests hidden gems tailored to individual tastes rather than following mainstream popularity trends. As a result, users often stumble upon new favorites that might have eluded them on other platforms.
The diversity of content on Banflix
Banflix has made a name for itself by offering an impressive range of content that appeals to diverse audiences. From blockbuster films to indie gems, there’s something for everyone.
The platform curates original series that push creative boundaries. Viewers can explore genres they may not typically watch—be it documentary, sci-fi, or romance—inviting them into new narratives and experiences.
International titles also shine on Banflix. Users can dive into foreign films and shows, enriching their viewing palette with unique cultural perspectives and storytelling styles.
Additionally, the service emphasizes diversity in representation. It actively seeks out voices from underrepresented communities, ensuring a rich tapestry of characters and stories is showcased throughout its library. This commitment resonates deeply with viewers looking for authenticity and relatability in what they watch.
User-friendly interface and features
Banflix boasts an intuitive interface that makes navigation a breeze. Users can easily browse through categories, ensuring they find something appealing in just moments. The layout is clean and visually engaging, drawing attention to the content without clutter.
One standout feature is its personalized recommendation system. As you watch more shows and movies, Banflix learns your preferences and curates suggestions tailored for you. This means less time searching and more time enjoying.
Additionally, the platform offers seamless integration across devices. Whether you’re on a smart TV or using a mobile phone, switching between devices feels effortless.
The search function enhances user experience as well. With filters for genre, release year, and ratings at your fingertips, finding hidden gems becomes simple. All these elements come together to create an inviting space that encourages exploration and binge-watching alike.
The impact of Banflix on the streaming industry
Banflix has undeniably shaken up the streaming landscape since its launch. With a focus on niche content and user engagement, it has carved out a unique position in a crowded market.
One significant impact is how Banflix encourages competition among existing platforms. Traditional giants are now re-evaluating their strategies to retain subscribers who crave something fresh and different.
Additionally, the service’s algorithm-driven recommendations have raised the bar for personalization. Users find themselves discovering hidden gems effortlessly, enhancing their viewing experience significantly.
The platform’s emphasis on diverse storytelling brings underrepresented voices to mainstream audiences. This shift not only broadens viewers’ horizons but also promotes inclusivity within entertainment.
As more creators flock to Banflix for opportunities, we can expect an exciting influx of innovative content that challenges conventional narratives in film and television. The dynamics of viewer expectations continue evolving as Banflix sets new trends in what audiences desire from their streaming subscriptions.
Criticisms and controversies surrounding Banflix
Banflix has certainly stirred the pot in the streaming world. The platform’s aggressive content acquisition strategy has raised eyebrows among industry veterans. Critics argue that this approach often prioritizes quantity over quality.
Another point of contention is its pricing model. Some users have expressed dissatisfaction with rising subscription fees, believing they don’t reflect the value delivered. This sentiment has sparked discussions on affordability and access.
Additionally, Banflix’s algorithm-driven recommendations have come under fire. Viewers sometimes feel trapped in a bubble, seeing only a narrow range of suggestions based on their viewing history.
Issues around censorship have also surfaced. Certain films and shows face removal or editing due to regional restrictions or compliance concerns, leaving some fans frustrated about losing beloved content from their libraries.
Future plans for Banflix and its potential growth
Banflix is poised for an exciting future. The platform has plans to expand its library significantly, introducing more exclusive content that appeals to a wider audience.
Collaborations with independent filmmakers are on the horizon. This strategy will bring fresh perspectives and innovative storytelling to viewers.
Additionally, Banflix aims to enhance its technology. Expect improvements in streaming quality and user experience. Features like personalized recommendations based on viewing habits could transform how users discover content.
International expansion is also part of the roadmap. By tapping into global markets, Banflix hopes to attract diverse subscribers who crave unique entertainment options from around the world.
Community engagement initiatives may foster a dedicated fan base. Interactive features such as watch parties and forums could create a sense of belonging among subscribers eager for connection through shared interests in film and series.
Conclusion
Banflix is making waves in the streaming universe, offering a unique blend of content and features that cater to diverse audiences. Its distinct approach sets it apart from traditional platforms and creates an engaging viewing experience.
The variety found on Banflix is impressive. Users can explore everything from indie films to mainstream blockbusters, as well as international shows that may not typically get attention elsewhere. This commitment to diversity enriches its library and draws in viewers looking for something different.
Navigating Banflix is a breeze thanks to its user-friendly interface. Simple menus and smart recommendations make it easy for users to find what they want quickly. The integrated social features also allow viewers to connect with friends, share their favorite finds, and discuss new releases seamlessly.
TECHNOLOGY
Unlocking the Power of Plangud: A Comprehensive Guide

Enter Plangud a revolutionary tool designed to streamline your planning and productivity like never before. Whether you’re an entrepreneur juggling multiple projects or a student managing assignments, Plangud offers a unique approach to organization that can transform how you work.
Imagine having all your tasks, deadlines, and goals in one place. Picture a system that not only helps you plan but also motivates you to achieve more each day. This is the power of Plangud. It combines simplicity with functionality, making it accessible for anyone who wants to enhance their workflow.
Curious about what makes this platform so special? Let’s dive deeper into the world of Plangud and explore how it can revolutionize your daily routine and boost your productivity!
The Benefits of Using Plangud
Plangud offers a range of benefits that can transform how you approach tasks. Its intuitive interface makes it easy for anyone to navigate and utilize effectively. This simplicity encourages more users to adopt the platform seamlessly.
One major advantage is its ability to enhance collaboration among team members. Everyone stays on the same page, reducing misunderstandings and boosting productivity. Real-time updates ensure that changes are visible instantly, fostering a sense of teamwork.
Additionally, Plangud promotes better time management through its scheduling features. Users can prioritize tasks efficiently, ensuring deadlines are met without unnecessary stress.
Moreover, the analytics tools provide valuable insights into progress and performance metrics. These data-driven reports help identify areas for improvement and streamline workflows further.
Using Plangud ultimately leads to increased efficiency in both individual and group projects. The platform’s versatility caters to diverse needs across various industries.
How to Get Started with Plangud
Getting started with Plangud is easy and straightforward. First, visit the official website to create an account. Registration typically requires just a few basic details.
Once you’re signed up, take some time to explore the platform’s features. Familiarize yourself with its user interface and tools designed for planning and organization.
Next, set your goals. Define what you want to achieve using Plangud—whether it’s managing projects or personal tasks.
Consider integrating existing data or materials into your new workspace. This can save time and help streamline your workflow from the get-go.
Don’t hesitate to check out tutorials or guides within the platform. These resources provide valuable insights that can enhance your experience right away.
Start small by creating simple plans before diving into more complex projects. Build confidence gradually while adapting Plangud to fit your unique needs.
Tips for Maximizing Productivity with Plangud
To truly harness the power of Plangud, start by setting clear and achievable goals. Break larger tasks into smaller steps to maintain focus and momentum.
Utilize the scheduling feature effectively. Block out specific times for different projects. This helps create a structured workflow that prevents distractions.
Leverage collaboration tools within Plangud. Engage with your team by sharing ideas or progress updates in real time. Communication is crucial for maintaining productivity.
Incorporate regular check-ins with yourself or your team to assess what’s working and what isn’t. Adjustments may be necessary along the way.
Familiarize yourself with keyboard shortcuts available in Plangud. They can significantly speed up navigation, allowing you more time for actual work rather than clicking around aimlessly.
Integrating Plangud into Your Daily Routine
Integrating Plangud into your daily routine can transform how you manage tasks. Start by setting aside a few minutes each morning to outline your day using the platform. This helps prioritize important activities.
Consider syncing Plangud with other tools you already use. Whether it’s email or calendar apps, integration streamlines processes and keeps everything in one place.
During work hours, take advantage of reminders for deadlines and meetings. This feature ensures that nothing slips through the cracks while keeping you focused on what matters most.
Make it a habit to review your progress at the end of each day. Reflecting on accomplishments fosters motivation and identifies areas for improvement.
Encourage colleagues or team members to adopt Plangud as well. A shared approach enhances collaboration and accountability within projects.
Case Studies: Successful Implementation of Plangud in Various Industries
Plangud has made waves across various industries by enhancing workflow and productivity. In the tech sector, a leading software company adopted Plangud to streamline project management. The result? A 30% reduction in time spent on task allocation.
In healthcare, a hospital integrated Plangud for scheduling staff shifts. This shift led to improved patient care through better resource management, allowing nurses and doctors to focus on what truly matters—patient well-being.
Retail businesses have also reaped benefits. One prominent chain utilized Plangud for inventory tracking and supply chain coordination. They experienced significant cost savings and minimized stockouts that often frustrated customers.
Even educational institutions embraced this tool. A university used Plangud to coordinate course offerings, resulting in higher student satisfaction rates due to streamlined class schedules and resources.
These examples showcase how versatile Plangud can be when tailored effectively across different fields.
Common Challenges and Solutions When Using Plangud
Using Plangud can transform productivity, but it’s not without its challenges. One common hurdle is user resistance. Many people hesitate to adopt new tools, fearing disruption in their workflow.
Training sessions and onboarding tutorials can help ease this transition. Comprehensive resources empower users to explore Plangud’s features confidently.
Another issue is integration with existing systems. Smooth functionality depends on seamless collaboration among various tools. It’s crucial to invest time in setting up integrations properly.
Technical glitches or bugs may arise during implementation as well. Regular updates from the developers often address these issues promptly, so staying informed about upgrades is essential.
Some users struggle with overwhelmed project views due to excessive task details. Customizing dashboards allows individuals to focus on what matters most while reducing visual clutter for increased clarity and efficiency.
Conclusion
Plangud has emerged as a powerful tool for individuals and businesses alike. Its versatility allows users to tailor their planning and productivity strategies effectively. By understanding how Plangud works, you open the door to numerous benefits that can transform your daily operations.
Getting started is straightforward, making it accessible even for those who may not consider themselves tech-savvy. With some initial setup and exploration of its features, users can begin reaping the rewards of enhanced organization and efficiency.
Maximizing productivity with Plangud involves integrating its various functionalities into your workflow seamlessly. Utilizing tips like setting specific goals or utilizing reminders can elevate your experience further. As you incorporate Plangud into your daily routine, you’ll find new ways to stay on track while minimizing stress.
TECHNOLOGY
Infector virus: How They Spread and Impact Our Lives
Viruses are tiny entities that can have a massive impact on our lives. From the common cold to more severe illnesses, these microorganisms are everywhere. They can spread quickly and affect millions of people in a matter of days. Among them, infector viruses stand out due to their ability to invade host cells and replicate efficiently.
Understanding how these viruses operate is crucial in today’s world, where global travel and interconnectedness make outbreaks more likely than ever. As we dive into the specifics of infector viruses, we’ll uncover how they spread and why it matters for our health and safety. Join us as we explore this fascinating yet concerning aspect of microbiology that affects us all.
What is an infector virus?
An infector virus is a type of microorganism that can invade living cells. Once inside, it hijacks the cell’s machinery to replicate itself. This process often leads to cell damage or death.
These viruses come in various shapes and sizes. Some are simple, while others have complex structures with protective coatings. Their ability to adapt makes them particularly challenging for our immune systems.
Infector viruses can affect a wide range of organisms, from humans and animals to plants and bacteria. They play significant roles in ecosystems but can also cause serious health issues.
Understanding how these viruses operate helps researchers develop vaccines and treatments. The study of infector viruses is crucial for public health as we navigate emerging threats around the globe.
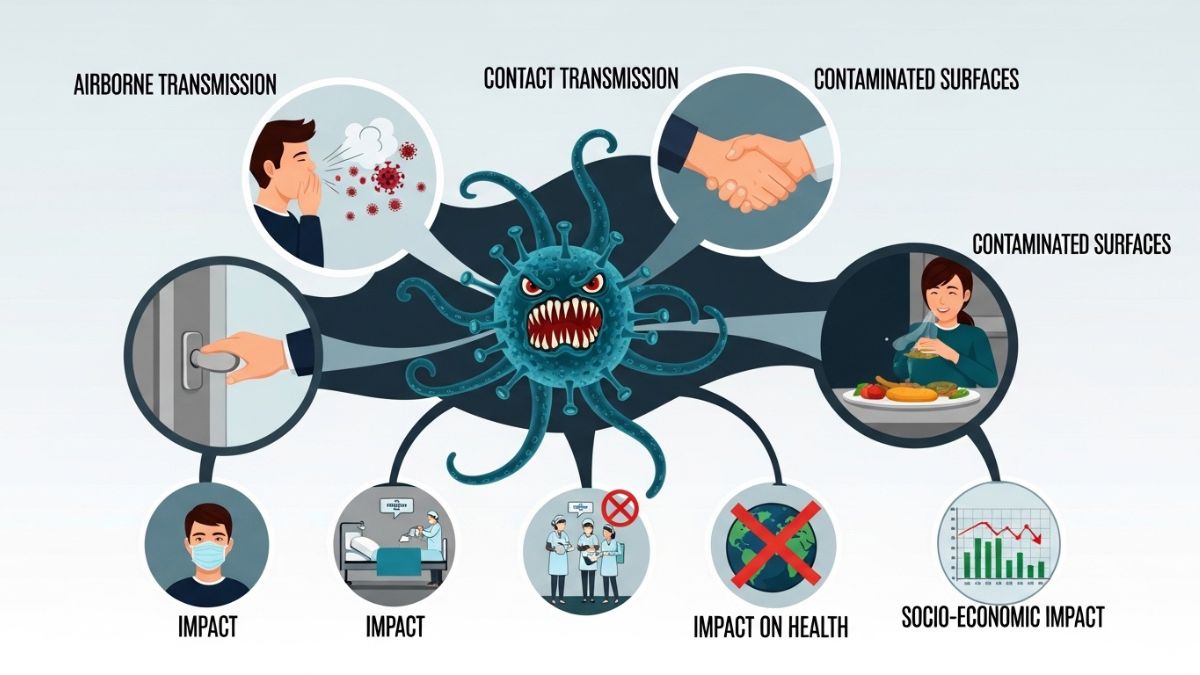
How do infector viruses spread?
Infector viruses can spread through various means, making them particularly challenging to control. One primary mode of transmission is direct contact. When an infected person touches another individual or a surface, the virus can transfer easily.
Airborne particles also play a significant role in spreading these viruses. As we breathe, talk, or cough, tiny droplets containing the virus become suspended in the air. Others may inhale these droplets without even realizing it.
Another common way infector viruses propagate is via contaminated surfaces and objects. Viruses can survive on doorknobs, phones, and utensils for hours or even days. Touching these surfaces and then touching your face increases the risk of infection dramatically.
Some infector viruses require vectors like insects to transmit between hosts. Mosquitoes are well-known carriers that facilitate this type of spread by biting an infected host and then transferring the virus to others they bite thereafter.
The effects of infector viruses on our health
Infector viruses can have profound effects on human health. They enter the body and exploit our cells for reproduction, often leading to illness. Symptoms may range from mild discomfort to severe conditions that require hospitalization.
Influenza is a prime example of an infector virus that causes seasonal outbreaks. It can lead to respiratory problems, fever, and fatigue. For vulnerable populations like the elderly or those with underlying health issues, these viruses pose even greater risks.
Moreover, some infector viruses can result in long-term health consequences. Conditions such as chronic fatigue syndrome or post-viral syndromes can linger well after initial infection has subsided.
The psychological impact shouldn’t be overlooked either; fear of viral outbreaks can contribute to anxiety and stress among communities. Awareness and understanding are crucial in navigating these challenges effectively.
Recent outbreaks of infector viruses
Recent outbreaks of infector viruses have captured global attention and concern. The rise in new strains has highlighted our vulnerability to these microscopic foes.
For instance, the emergence of novel coronaviruses has led to significant disruptions worldwide. Each outbreak brings about unique challenges in containment and response efforts.
Influenza variants also continue to circulate, reminding us that vigilance is necessary year-round. Health organizations are constantly monitoring changes in viral behavior and transmission rates.
In regions with dense populations, the spread can be rapid and devastating. Vaccination campaigns play a crucial role in mitigating risks during peak seasons.
Social distancing measures have become commonplace during such crises, but they come with economic costs as well. The interconnectedness of our world means that an outbreak anywhere can quickly turn into a global issue.
Efforts for better surveillance systems are underway to track these viruses more effectively, aiming for quicker responses when outbreaks occur.
How to protect against infector viruses
Staying vigilant is key when it comes to protecting yourself from infector viruses. Start with good hygiene practices. Frequent hand washing with soap for at least 20 seconds can significantly reduce your risk of infection.
Consider using hand sanitizer, especially in crowded places where soap and water aren’t available. Choose one that contains at least 60% alcohol for maximum effectiveness.
Vaccination plays a crucial role as well. Stay updated on recommended vaccines that protect against specific viruses prevalent in your area or traveling destination.
Avoid close contact with sick individuals whenever possible. Maintain a safe distance during outbreaks, and don’t hesitate to wear masks if advised by health authorities.
Keep informed about local health advisories and follow any guidelines provided by public health officials. Awareness helps you make better choices to stay healthy amidst potential threats from infector viruses.
Conclusion
Viruses are tiny entities that wield significant influence over our lives. Among them, infector viruses stand out due to their ability to cause illness and outbreaks. Understanding these viruses is crucial for safeguarding ourselves and our communities.
An infector virus is a type of pathogen known for its capacity to invade host cells, replicate, and spread throughout populations. They can be responsible for a broad spectrum of diseases, from mild infections like the common cold to more severe illnesses such as COVID-19 or influenza.
These viruses spread through various means—airborne transmission via respiratory droplets, direct contact with infected surfaces, or even through bodily fluids. Their adaptability allows them to find new hosts quickly and efficiently.
The impact on health can vary significantly depending on the specific virus in question. Symptoms might range from mild discomfort to severe illness requiring hospitalization. Vulnerable groups such as the elderly or those with pre-existing conditions often face heightened risks.
-

 HEALTH2 years ago
HEALTH2 years agoTransformative Health Solutions: Unveiling the Breakthroughs of 10x Health
-

 GENERAL2 years ago
GENERAL2 years agoDiscovering the Artistic Brilliance of Derpixon: A Deep Dive into their Animation and Illustration
-

 Posts2 years ago
Posts2 years agoSiegel, Cooper & Co.
-

 Lifestyle2 years ago
Lifestyle2 years agoPurenudism.com: Unveiling the Beauty of Naturist Lifestyle
-

 FASHION2 years ago
FASHION2 years agoThe Many Faces of “λιβαισ”: A Comprehensive Guide to its Symbolism in Different Cultures
-

 Lifestyle2 years ago
Lifestyle2 years agoBaddieHub: Unleashing Confidence and Style in the Ultimate Gathering Spot for the Baddie Lifestyle
-

 Entertainment2 years ago
Entertainment2 years agoGeekzilla Podcast: Navigating the World of Pop Culture, Gaming, and Tech
-

 Lifestyle2 years ago
Lifestyle2 years agoSandra orlow: Unraveling the Story of an Iconic Figure
